Reverse proxies typically act as a gateway for incoming connections to an organization’s network servers, preventing direct connections from clients outside the firewall to servers inside the firewall. The reverse proxy can enhance security, by restricting protocols and logging connection activity. Reverse proxies may also act as caches to respond to common requests. In some cases, multiple reverse proxies may be deployed to cache results from one server, as a form of load balancing. Figure 12-2 shows how clients connect through a reverse proxy.
Figure 12-2: Connecting through a reverse proxy
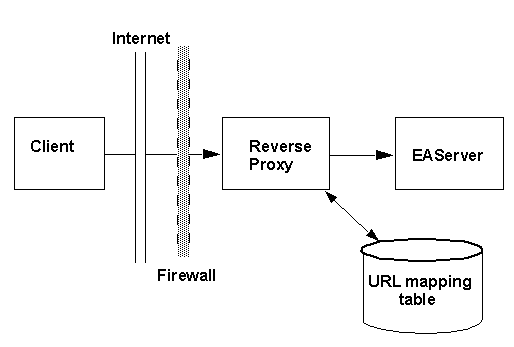
Clients connect to EAServer through a reverse proxy as follows:
The client connects to the reverse proxy, and sends each IIOP packet tunnelled inside an HTTP or HTTPS packet. The destination server address is encoded in the HTTP packet header as:
GET /host/port/HIOP/1.0/...
Where host is the target EAServer host name, and port is the target EAServer port number.
The reverse proxy uses its URL mapping configuration (shown as a database in the figure) to determine the destination server address.
The reverse proxy opens a connection to the destination server, or reuses an existing connection, and forwards the request to the server, then forwards the response to the client.