

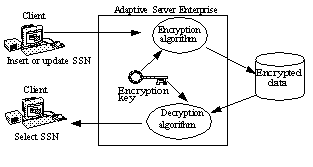
Figure 1 displays a high-level look at encryption and decryption processing in Adaptive Server. In this example, the Social Security Number (SSN) is being updated and encrypted:
Figure 1: Encryption and decryption in Adaptive Server
To create encryption keys, use create encryption key, which:
Internally creates a symmetric key for the specified length of the key using the Security Builder Crypto™ API.
Stores the key in encrypted form in the system catalog sysencryptkeys.
Adaptive Server keeps track of which key is used to encrypt a given column. Column encryption uses a symmetric encryption algorithm, which means that the same key is used for encryption and decryption.
When you insert or update data in an encrypted column, Adaptive Server transparently encrypts the data immediately before writing the row. When you select from an encrypted column, Adaptive Server decrypts the data after reading it from the row. Integer and floating point data are encrypted in a canonical form:
Most significant bit (MSB) format for integer data.
Institute of Electrical and Electronics Engineers (IEEE) floating point standard with MSB format for floating point data.
Data encrypted on one platform may be decrypted on another platform, provided that both platforms use the same character set.
To use encrypted columns in Adaptive Server:
Install the license option ASE_ENCRYPTION. See the Adaptive Server Enterprise Installation Guide for information.
Enable encryption in Adaptive Server Enterprise:
sp_configure 'enable encrypted columns', 0|1
0 – disable encryption.
1 – enable encryption.
Restart the server after you set this option.
If you turn off this option in a server that contains encrypted columns, any commands against these columns fail with an error message. Both the configuration parameter and the license option are needed to use encrypted columns. Only the System Security Officer can enable encrypted columns.
Set the system encryption password for a database using sp_encryption. See “Setting the system encryption password”.
Create the key for encrypting columns. See “Creating encryption keys”.
Specify the columns for encryption. See “Specifying encryption on new tables” and “Encrypting data in existing tables”
Grant decrypt permission to users who must see the data. See “Permissions for decryption”.
| Copyright © 2005. Sybase Inc. All rights reserved. |

|
|