The key custodian, who must be assigned the keycustodian_role, maintains encryption keys. Using the keycustodian_role role allows you to separate the duties for administering confidential data by ensuring that no administrator has implicit access to data. Figure 7-1 illustrates that the database owner, as the schema owner, controls permissions for accessing the data, but has no access without knowledge of the key’s password. The key custodian, however, administers keys and their passwords, but has no permissions on the data. Only the qualified end user, with permissions on the data and knowledge of the encryption key's password, can access the data.
Figure 7-1: Database owner controlling permissions for data
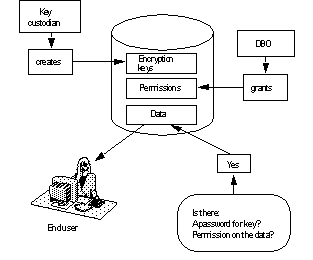
The system administrator and database owner do not have implicit key management responsibilities. Adaptive Server provides the system role keycustodian_role so that the SSO need not assume all encryption responsibity. The key custodian owns the encryption keys, but should have no explicit or implicit permissions on the data. The database owner grants users access to data through column permissions, and the key custodian allows users access to the key’s password. keycustodian_role is automatically granted to sso_role and can be granted by a user with the sso_role.
The key custodian can:
Create and alter encryption keys.
Assign as the database default key a key he or she owns, as long as he or she also owns the current default key, if one exists.
Set up key copies for designated users, allowing each user access to the key through a chosen password or a login password.
Share key encryption passwords with end users.
Grant schema owners select access to encryption keys on keys owned by the key custodian.
Create the master key or set the system encryption password.
Recover encryption keys.
Drop his or her own encryption keys.
Change ownership of keys he or she owns.
You can have multiple key custodians, who each own a set of keys. The key custodian grants the schema owner permission to use the keys on create table, alter table, and select into, and may disclose the key password to privileged users or allow users to associate key copies with a personal password or a login password. The key custodian can work with a “key recoverer” to recover keys in the event of a lost password or disaster. If the key custodian leaves the company, the SSO can use the alter encryption key command to change key ownership to a new key custodian.