There are two keys between the user and the data: the database-encryption key (DEK) or column-encryption key (CEK) and the key-encryption key (KEK). The DEK and CEK encrypts data and users must have access to it before they can access encrypted data.
It cannot be stored on disk in an unencrypted form. Instead, SAP ASE uses a KEK, or 2 KEKs in dual control, to encrypt the DEK or CEK when you create or alter an encryption key. The KEK also decrypts the DEK or CEK before you can access decrypted data. DEKs and CEKs are stored in encrypted form in sysencryptkeys.
The KEK is a master key, created separately by the system security officer or key custodian, is an internally derived key from the system encryption password, a user-specified password, or a login password, depending on how you specify the key’s encryption with the create and alter encryption key statements. Both the system encryption password and the master key are stored in encrypted form.
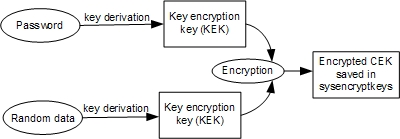
The following figure describes how to create and store a column encryption key for a create encryption key statement. The KEK is derived from a password and the KEK and the raw CEK are fed into the encryption function to produce an encrypted CEK.
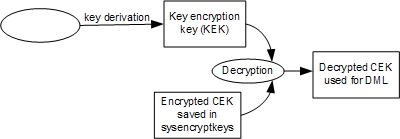
The following figure describes how the KEK is used during a DML operation to decrypt the CEK. The raw CEK is then used to encrypt or decrypt data.