Import, export, and generate the X.509 certificates that secure
communication paths between SAP Mobile Server and the SAP enterprise
information system (EIS), and for client authentication, including single sign-on (SSO) with
X.509 or SSO2 tokens.
Creating, Importing, and Exporting Certificates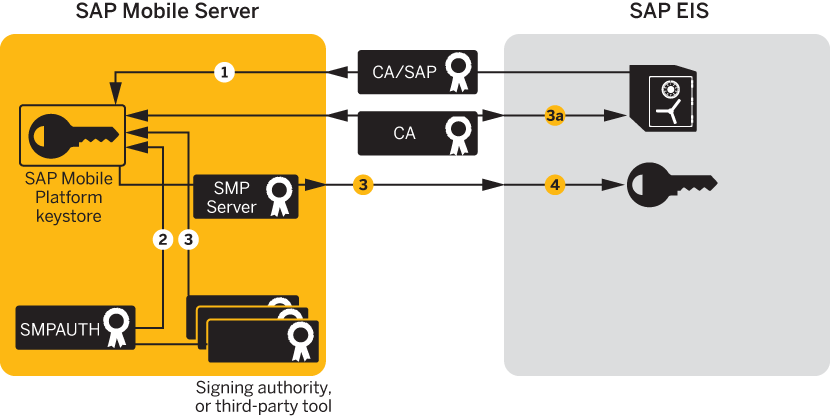
Use SAP Control Center to import these certificates into the
SAP Mobile Server keystore. See Managing Certificates for SSL Encryption.
- Import SAP CA certificates into the SAP Mobile Server keystore, including:
- The standard SAP/DOE server root certificate (.crt or .cer) required to
establish a trusted relationship between
SAP Mobile Server and the SAP EIS.
- Any CA certificate used to sign .pse certificates used for JCo/SNC communications.
- For Gateway deployments where SAP Mobile Server
is the Online Data Proxy (ODP), import the Gateway server's CA into the
keystore of SAP Mobile Platform.
The ODP requires two certificate files: one that
contains the certificate and private key for use by the server, and
another that contains only the certificate for use by clients. The
certificates should be in the form of a PKCS#12 file using an RSA
key pair (key lengths in the range of 512–16384 are supported), in
PEM or DER format. The key usage should be set to Key Encipherment,
Data Encipherment, Key Agreement (38).
- Any other required SAP CA certificate. For example, any CA certificate used to
sign a client certificate that is to be authenticated by SAP Mobile Server must be imported if you are
implementing SSO with X.509.
Note: If SAP Mobile Server is communicating with a
server that is hosting a Web service that is bound to SAP function
modules, import that server's CA certificate into the SAP Mobile Server keystore.
- Import the certificate and private key (PKCS #12) issued by the SAP system
administrator into the SAP Mobile Server
keystore. This certificate secures communications for packages and is used when
a user uses an X.509 certificate rather than a user name and password. For
example:
Even if the EIS administrator is using the native SAP public-key
infrastructure (PKI) to generate certificates, you must still import them into
the SAP Mobile Server keystore. The certificate
name,
SUPAUTH and alias,
CERTALIAS represent the type of package/client to
be authenticated, for example:
- TechnicalUser certificate with doectech alias – a
DOE-C package
client.
- SAPUser certificate with SAPClient alias – a SAP or Web
service MBO package client.
- Create and import the SUPServer certificate into the
SAP Mobile Server keystore. For example:
Note: (3b) You can create the SUPServer certificate using a
third-party tool such as OPENSSL, or the signing authority used to create
all SAP server certificates, in which case you need not import any other CA
signing authority certificate into the SAP Mobile Server keystore. However, if you create the SUPServer
certificate with another CA signing authority, you must import that CA
certificate into both the SAP Mobile Server
keystore, and into the SAP Server using the STRUST transaction.
- Import the SUPServer certificate into SAP/DOE server using the STRUST transaction.
You can now configure your environment for mutual authentication and SSO, in
which any client connecting to SAP Mobile Server presents
credentials, and a server certificate (SUPAUTH) is selected for
SAP Mobile Server to present to clients.

