If you require multiple identity files, you can improve security and extensibility by using certificate chains instead of self-signed certificates. Certificate chains require a Certificate Authority or an enterprise root certificate to sign identities.
See Self-signed root certificates.
Certificate chains provide the following advantages:
Extensibility For server authentication, you can configure clients to trust any certificate signed by an enterprise root certificate or Certificate Authority. If you add a new MobiLink or database server, clients do not require a copy of the new certificate.
Security The enterprise root certificate's private key is not in the identity file. Storing the root certificate's private key in a high-security location, or using a Certificate Authority with dedicated facilities, protects the integrity of server authentication.
The following diagram provides the basic enterprise root certificate architecture.
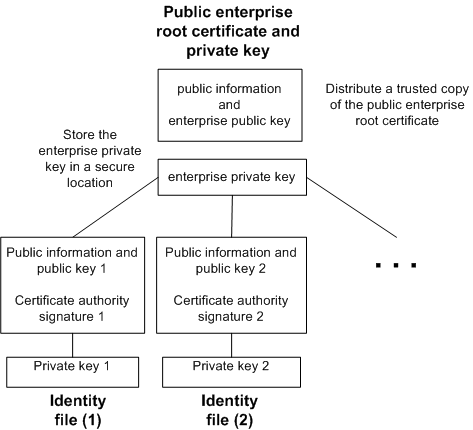
To create certificates used in a multi-server environment:
Generate a public enterprise root certificate and enterprise private key.
Store the enterprise private key in a secure location, preferably a dedicated facility.
For server authentication, you distribute the public enterprise root certificate to clients.
Use the enterprise root certificate to sign identities.
Use the public enterprise root certificate and enterprise private key to sign each identity. For server authentication, the identity file is used for the server.
You can also use a third-party Certificate Authority to sign your server certificates. Commercial Certificate Authorities have dedicated facilities to store private keys and create high-quality server certificates.
Enterprise root certificates
Signed identity files
| Discuss this page in DocCommentXchange. Send feedback about this page using email. |
Copyright © 2009, iAnywhere Solutions, Inc. - SQL Anywhere 11.0.1 |