

All the information related to keys and encryption is encapsulated by the create encryption key, which allows you to specify the encryption algorithm and key size, the key's default property, as well as the use of an initialization vector or padding during the encryption process.
Column encryption in Adaptive Server uses the Advanced Encryption Standard (AES) symmetric key encryption algorithm, with available key sizes of 128, 192, and 256 bits. Random key generation and cryptographic functionality is provided by Security Builder Crypto™ API.
You can create separate keys for each encrypted column. Keys can be shared between columns, but each column can have only one key. To encrypt one column using an initialization vector and one column without using an initialization vector, create two separate keys, one that specifies use of an initialization vector and one that specifies no initialization vector.
The System Security Officer uses the as default clause in the create encryption key to set a default encryption key for the database. The default key is used whenever the encrypt qualifier is used without a key name on create table or alter table.
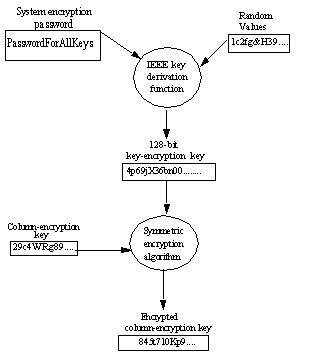
To securely protect key values, Adaptive Server uses the system encryption password to generate a 128-bit key-encrypting key, which in turn is used to encrypt the newly created key. The column-encryption key is stored in encrypted form in the sysencryptkeys system table.
Figure 2: Encrypting user keys
The syntax for create encryption key is:
create encryption key keyname [as default] for algorithm [with [keylength num_bits] [init_vector [null | random]] [pad [null | random]]]
where:
keyname – must be unique in the user’s table, view, and procedure name space in the current database.
as default – allows the System Security Officer to create a database default key for encryption. This enables the table creator to specify encryption without using a keyname on create table, alter table and select into. Adaptive Server uses the default key from the same database. The default key may be changed. See “alter encryption key”.
algorithm – Advanced Encryption Standard (AES) is the only algorithm supported. AES supports key sizes of 128 bits, 192 bits, and 256 bits and a block size of 16 bytes.
keylength num_bits – the size, in bits, of the key to be created. For AES, valid key lengths are 128, 192, and 256 bits. The default keylength is 128 bits.
init_vector random – specifies use of an initialization vector during encryption. When an initialization vector is used by the encryption algorithm, the ciphertext of two identical pieces of plaintext are different, which prevents a cryptanalyst from detecting patterns of data. Use of an initialization vector can add to the security of your data.
An initialization vector has some performance implications. Index creation, and optimized joins and searches, can be performed only on a column whose encryption key does not specify an initialization vector. See “Performance considerations”.
init_vector null – omits the use of an initialization vector when encrypting. This makes the column suitable for supporting an index.
The default is to use an initialization vector, that is, init_vector random. Use of an initialization vector implies using a cipher block chaining (CBC) mode of encryption; setting init_vector null implies the electronic code book (ECB) mode.
pad null – is the default. It omits random padding of data.
You cannot use padding if the column must support an index.
pad random – data is automatically padded with random bytes before encryption. You can use padding instead of an initialization vector to randomize the ciphertext. Padding is suitable only for columns whose plaintext length is less than half the block length. For the AES algorithm the block length is 16 bytes.
For example, to specify a 256-bit key called “safe_key” as the database default key, the System Security Officer enters:
create encryption key safe_key as default for AES with keylength 256
The following example creates a 128-bit key called “salary_key” for encrypting columns using random padding:
create encryption key salary_key for AES with init_vector null pad random
This example creates a 192-bit key named “mykey” for encrypting columns using an initialization vector:
create encryption key mykey for AES with keylength 192 init_vector random
The System Security Officer has default permission to create encryption keys and may grant that permission to other users.
For example:
grant create encryption key to key_admin_role
| Copyright © 2005. Sybase Inc. All rights reserved. |

|
|