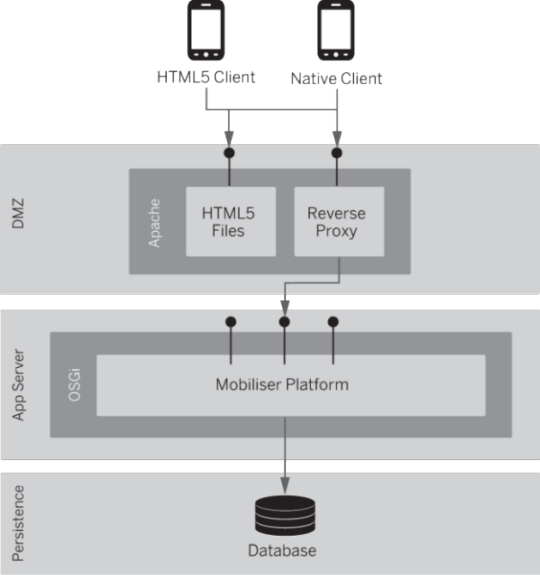
Any reverse proxy, such as Apache HTTPD, can accept incoming requests from the Internet in the DMZ and forward them to the Mobiliser core running on the application server tier.
<Proxy *> Order deny,allow Allow from all </Proxy> ProxyPass /mobiliser/smartphone http://localhost:8080/mobiliser/smartphone ProxyPassReverse /mobiliser/smartphone http://localhost:8080/mobiliser/smartphone ProxyPass /mobiliser/rest/smartphone http://localhost:8080/mobiliser/rest/smartphone ProxyPassReverse /mobiliser/rest/smartphone http://localhost:8080/mobiliser/rest/smartphone ProxyPass /mobiliser/binary http://localhost:8080/mobiliser/binary ProxyPassReverse /mobiliser/binary http://localhost:8080/mobiliser/binary ProxyPass /mobiliser/rest/binary http://localhost:8080/mobiliser/rest/binary ProxyPassReverse /mobiliser/rest/binary http://localhost:8080/mobiliser/rest/binary
In addition to shielding direct access to the core, the Apache server can provide access to the HTML5 version used by a smartphone, or any other HTML5 application. The same origin policy requires that the HTML files and the Ajax services be provided by the same server (host name + port). See http://en.wikipedia.org/wiki/Same_origin_policy.
The reverse proxy can also be used for SSL termination. When you deploy Mobiliser in the standard reverse proxy model, you must also make changes to the configuration on the Apache Web UI server (located on the DMZ layer) and one of the database preferences (located in the persistence layer).