Import, export, and generate the X.509 certificates that secure communication paths between Unwired Server and the SAP enterprise information system (EIS), and for client authentication, including single sign-on (SSO) with X.509 or SSO2 tokens.
Creating, Importing, and Exporting Certificates
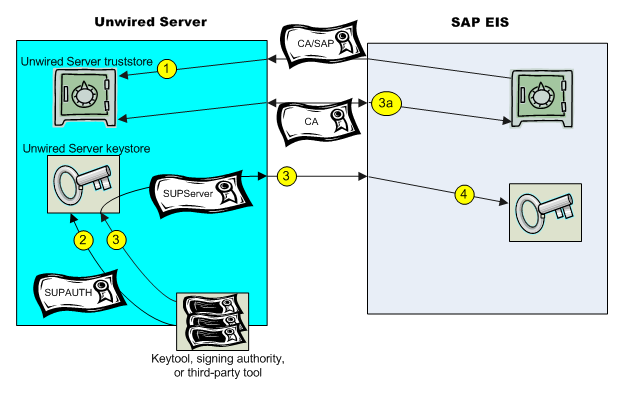

Use Java keytool commands to import these certificates into the Unwired Server truststore and keystore.
You can now configure your environment for mutual authentication and SSO, in which any client connecting to Unwired Server presents credentials, and a server certificate (SUPAUTH) is selected for Unwired Server to present to clients.