The secure connection between a client and a server can be used for login authentication and message protection.
Figure 5-1: Establishing secure connections between a client and Adaptive Server
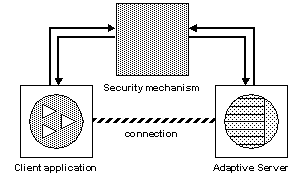
If a client requests authentication services:
The client validates the login with the security mechanism. The security mechanism returns a credential, which contains security-relevant information.
The client sends the credential to Adaptive Server.
Adaptive Server authenticates the client’s credential with the security mechanism. If the credential is valid, a secure connection is established between the client and Adaptive Server.
If the client requests message protection services:
The client uses the security mechanism to prepare the data packet it sends to Adaptive Server.
Depending upon which security services are requested, the security mechanism might encrypt the data or create a cryptographic signature associated with the data.
The client sends the data packet to Adaptive Server.
Upon receiving the data packet, Adaptive Server uses the security mechanism to perform any required decryption and validation.
Adaptive Server returns results to the client, using the security mechanism to perform the security functions that were requested; for example, Adaptive Server may return the results in encrypted form.