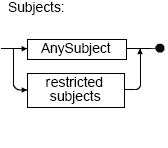
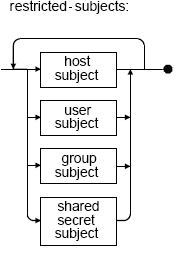
"Subjects": The empty "AnySubject" element (<AnySubject/>) creates a rule that applies to any host, user, or user group that attempts to perform the specified action on the specified resource. To restrict the rule to certain hosts, users, or user groups, use one or more host-subject, user-subject, and/or group-subject elements instead of "AnySubject".
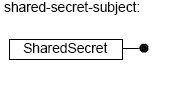
Specify a special empty shared-secret-subject (specified as <SharedSecret/>) once at the beginning of the ACL file to enable Sybase CEP Server connectivity.
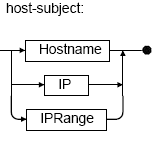
host-subject elements include "Hostname", "IP" and "IPRange" elements. You can specify any number of these in any combination in a single "Target" element.
Note: Specifying Subjects to Connect to the Local Computer: Because of differences in the way that Microsoft Windows and UNIX-like operating systems handle connections to the local machine, Sybase advises that you configure subjects connecting to the local machine either with both the loopback IP address 127.0.0.1 and the external IP address, or with both localhost and the external host name.
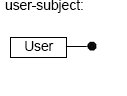
user-subject elements include the "User" element. You can specify any number of "User" elements in a single "Target" element.
Note: User credentials are sent over the network as unencrypted text. To protect the user credentials from network analyzers, enable the Secure Socket Layer (SSL). See
"Configuring SSL Support" for more information about enabling SSL.
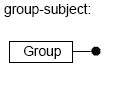
group-subject elements include the "Group" element. You can specify any number of "Group" elements in a single "Target" element.
If you specify multiple subjects in a single "Target", the rule applies to any host, user, or group that meets the criteria for at least one subject specification from each of the included groups. For example, a "Target" that includes a "Hostname" subject, an "IPRange" subject, and two "User" subjects applies to either of the indicated users when the computer from which they try to access the resource either matches the "Hostname" or falls within the "IPRange".
Here are some examples of "Subjects" elements:
<Subjects>
<AnySubject/>
</Subjects>
<Subjects>
<Hostname>.*\.sybase\.com</Hostname>
</Subjects>
<Subjects>
<IP>192.168.10.10</IP>
<IPRange>192.168.0.12/24</IPRange>
</Subjects>
<Subjects>
<IP>192.168.10.10</IP>
<User>jdoe</User>
<Group>qagroup</Group>
</Subjects>
"Resources": The empty "AnyResource" element (specified as <AnyResource/>) creates a rule that applies to any Sybase CEP Server resource requested by one of the subjects. To restrict the rule to certain resources, use the "Server", "Workspace", "Project", and/or "Stream" elements, in any combination. (The "Server" resource setting is typically used in conjunction with the "Connect" action, to permit or deny access to Sybase CEP Server.)
If you identify multiple resources, the subjects are allowed or denied access to any of the specified resources. For more information about how a resource hierarchy is used to grant or deny access to various resources, see "ACL Policy Set Implementation".
Here is an example of a "Resources" element:
<Resources>
<Stream>Production/.*/StreamIn</Stream>
<Stream>Production/.*/StreamOut</Stream>
</Resources>
"Actions": The "AnyAction" element (specified as <AnyAction/>) creates a rule that applies to any actions that the subject attempts on the specified resource. To restrict the rule to certain actions, use the "Connect", "Read", "Write", "Start/Stop", "Create/Destroy", and/or "GetStatus" elements, in any combination. If you identify multiple resources, the subjects are allowed or denied access to any of the specified actions. All elements contained inside an "Actions" element are empty. Here is an example of an "Actions" element:
<Actions>
<StartStop/>
</Actions>
Action requests are interrelated. The ability to perform certain actions depends on access to certain other types of actions:
-
Connection to a resource should be enabled in order to allow any other action on that resource. Connections can be enabled explicitly by using the "Connect" action, or by using the "AnyAction" action. If the connection is not enabled, the subject is not allowed to perform actions on the resource, even if a rule states that those actions are permitted.
-
To enable "GetStatus" for a status stream, the subject should also be enabled to "Read" from the status stream.
-
To enable SOAP calls to access resources, the resource should also be enabled to "GetStatus", "StartStop" or "Read".