The database file is composed of pages: fixed size portions of hard disk. The checkpoint log is located at the end of the database file and is stored in the system dbspace. Pages are added to the checkpoint log as necessary during a session, and at the end of the session, a history of the checkpoint log usage is stored in the database. This history is used to determine an appropriate size for the checkpoint log in future sessions.
Before any page is updated (made dirty), the database server performs the following operations:
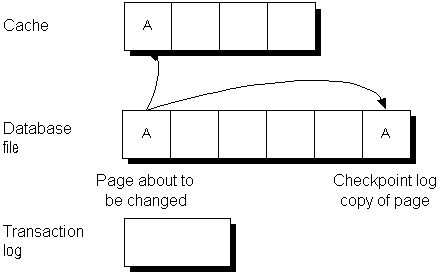
It reads the page into memory, where it is held in the database cache.
It makes a copy of the original page. These copied pages are the checkpoint log.
Changes made to the page are applied to the copy in the cache. For performance reasons they are not written immediately to the database file on disk.
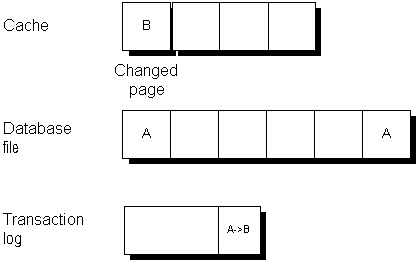
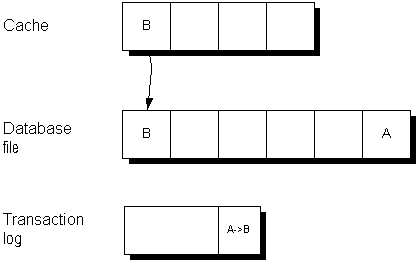
When the cache is full, the changed page may get written out to disk. The copy in the checkpoint log remains unchanged.
 See also
See also |
Discuss this page in DocCommentXchange.
|
Copyright © 2012, iAnywhere Solutions, Inc. - SQL Anywhere 12.0.1 |